Update: I was rightly corrected by the creator of uBlock, those are not links, but CSS selectors inside a <style> tag, to cause the offending links to be removed from the page. Furthermore, those particular rules are being fed from AdBlock Plus’ EasyList, and they are not related to uBlock.
I was tweaking a Jekyll theme to match the style of our Bootstrap-based site, when I suddenly noticed an alarming links to porn/spam sites, visible inside Chrome tools:
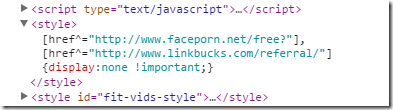
Alarmed, I didn’t know what to make of this at first. It’s a custom (paid) Bootstrap theme, so I suspected either the theme or one of its plugins was the culprit, however I could not find any code that seemed to inject this particular style.
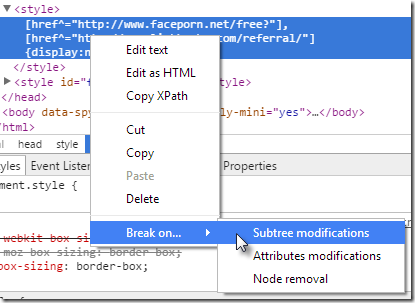
Armed with fairly little knowledge of dealing with web development, I decided to try and set a breakpoint inside the Chrome tools on the text inside the <style> element itself, by right-clicking and selecting Break on - Subtree modifications:
I reloaded the page and then found myself inside a script called contentscript-start.js, which turned out to belong to uBlock Origin:
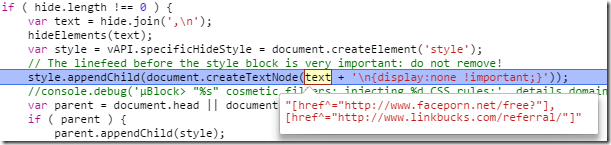
Thanks to George Pollard (@porges) I was led to this issue on the uBlock github, where it seemingly replaces all instances of http://face* with a matching filter (which, in this case, a link to a porn site). The reason for this is still unclear to me, as face* generates way more false positives (i.e. facebook).
This also explains the other link: the bottom of my Bootstrap page contains a link to the Facebook and LinkedIn pages. uBlock must be matching http://link* as well.
So if you find those while looking at your site through Chrome Dev Tools, don’t be alarmed as I was - it’s just your friendly neighborly adblock in action!